Visa Credit Card Hack
Mar 15, 2016 With a simple Google search you can get passwords, hacking tools, and even credit card information. After that, you are good to go! Just click on the button and check your Visa card. The money should now be added. This works for all countries. Currently it is mostly tested and used in USA. This is where the hack has been developed, tested and is currently being updated the most. However, it can be used all over the world.
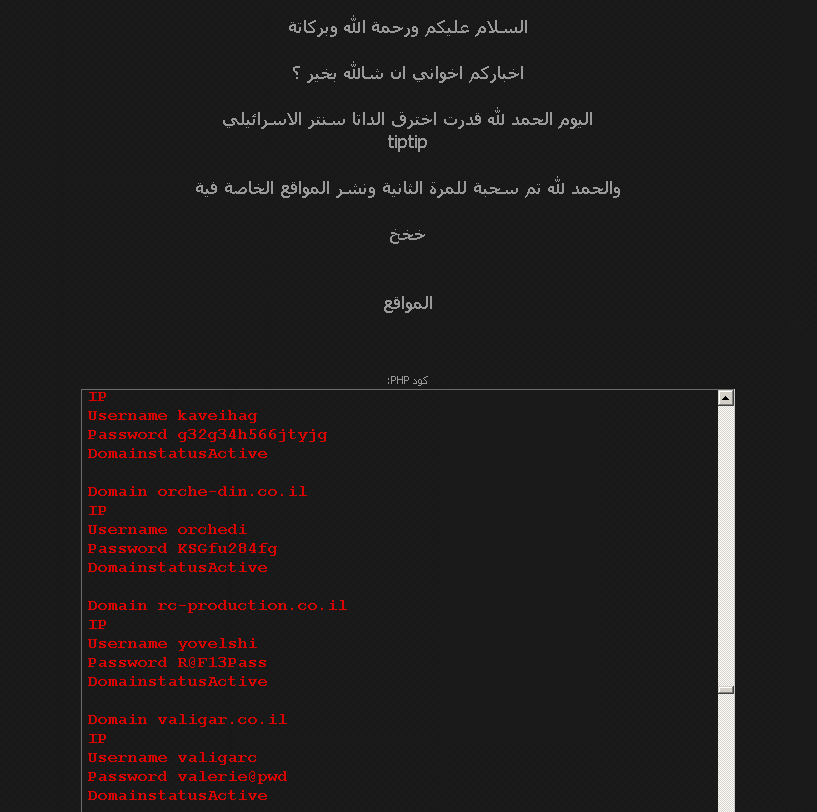
Hacked Visa Credit Card Numbers
We present an attack on hardware security modules used by retail banks for the secure storage and verification of customer PINs in ATM (cash machine) infrastruc- tures. By using adapti ve decimali sation tables and guess es, the maxim um amount of information is learnt about the true PIN upon each guess. It takes an average of 15 guesses to determine a four digit PIN using this technique, instead of the 5000 guess es intende d. In a single 30 min ute lunch- break, an attac ker can thus discov er appro ximate ly 7000 PINs rather than 24 with the brute force method.
Automatic Teller Machines (ATMs) are used by millions of customers every day to make cas h wit hdra wa ls fro m thei r acco unt s. Ho we ve r, the wid e depl oy men t and som eti mes secluded locations of ATMs make them ideal tools for criminals to turn traceable electronic money into clean cash. The customer PIN is the primary security measure against fraud; forgery of the mag- neti c stri pe on cards is triv ial in com pari son to PIN acqui sit ion.
Let it be the replacements rar. A street crimi nal can easily steal a cash card, but unless he observes the customer enter the PIN at an ATM, he can only have three guesses to match against a possible 10,000 PINs and would rarely strik e it luck y. Even when successful, his theft still cannot exceed the daily withdra wal limit of around. However, bank programmers have access to the computer systems tasked with the secure storage of PINs, which normally consist of a mainframe connected to a “Hardware Security Module” (HSM) which is tamper-resistant and has a restricted API such that it will only respond to with a YES/NO answer to a customer’s guess. A crude method of attack is for a corrupt bank programmer to write a program that tries all PINs for a particular account, and with average luck this would require about 5000 transactions to discover each PIN. A typical HSM can check maybe 60 trial PINs per second in addition to its normal load, thus a corrupt employee executing the program during a 30 minute lunch break could only make off with about 25 PINs.
However, HSMs implementing several common PIN generation methods have a flaw. The first ATMs were IBM 3624s, introduced widely in the US in around 1980, and most PIN genera tio n meth ods are bas ed upon thei r app roac h. The y cal cul ate the custom er’s original PIN by encrypting the account number printed on the front of the customer’s ca rd wi th a sec ret DE S ke y cal le d a “PI N gen era ti on k ey ”. Th e res ul ti ng ci phe rte xt 3.